![PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man](https://thecybersecuritymancom.files.wordpress.com/2018/08/evil-twin.png?w=925)
PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man

A single supervised learning model to detect fake access points, frequency sweeping jamming and deauthentication attacks in IEEE 802.11 networks - ScienceDirect
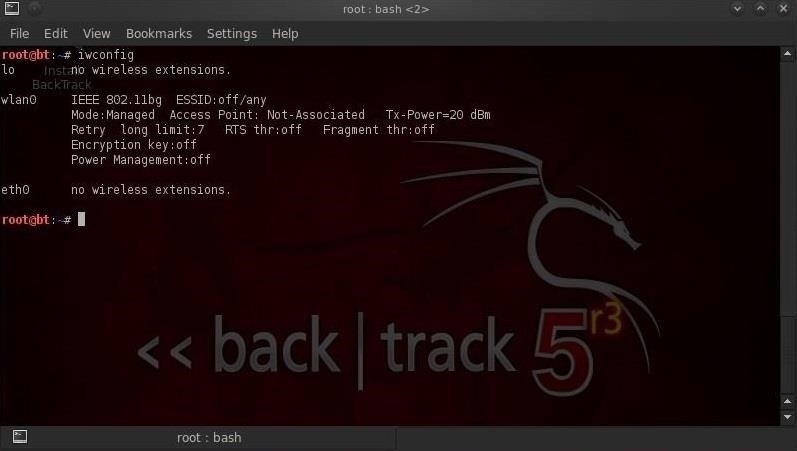
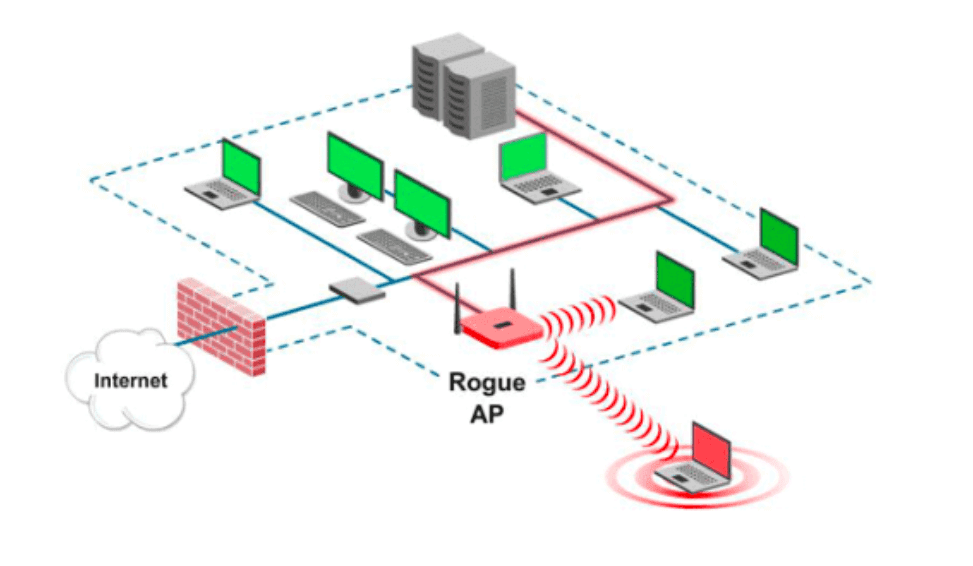


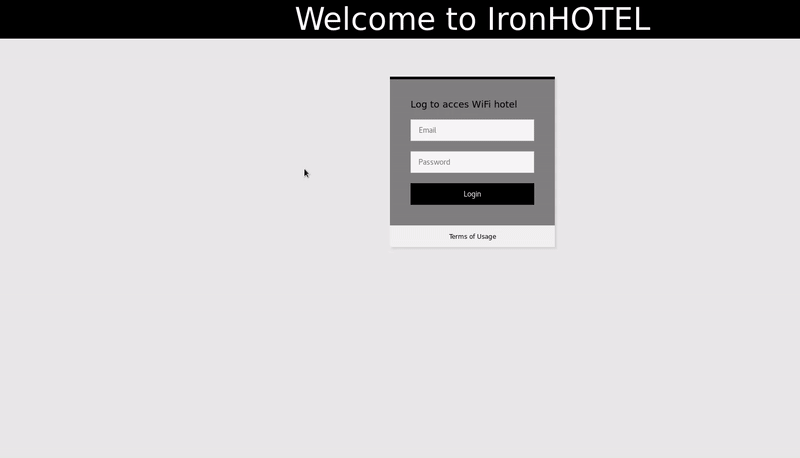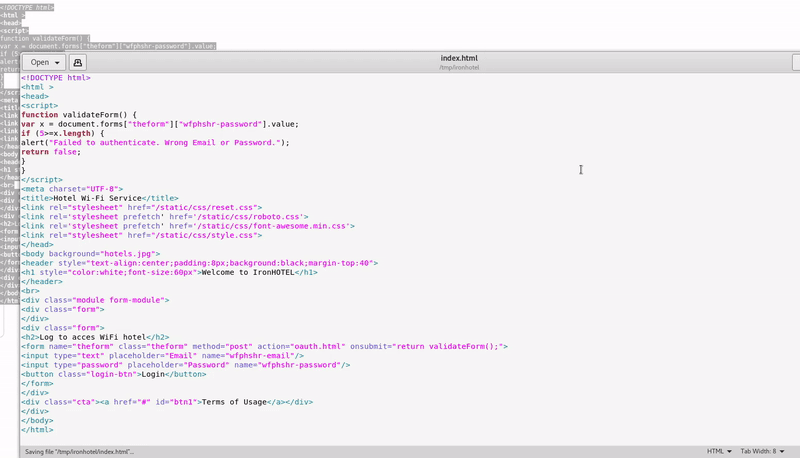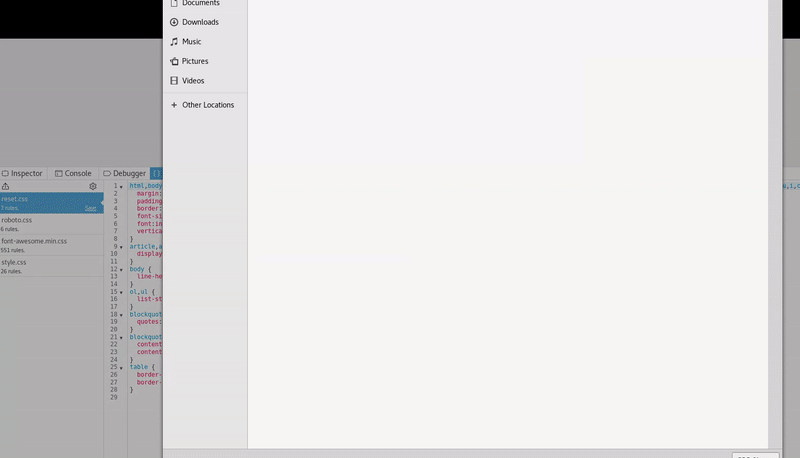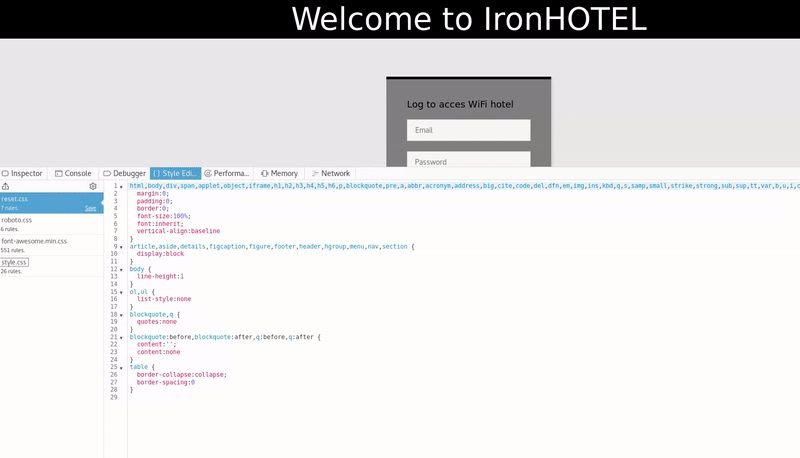



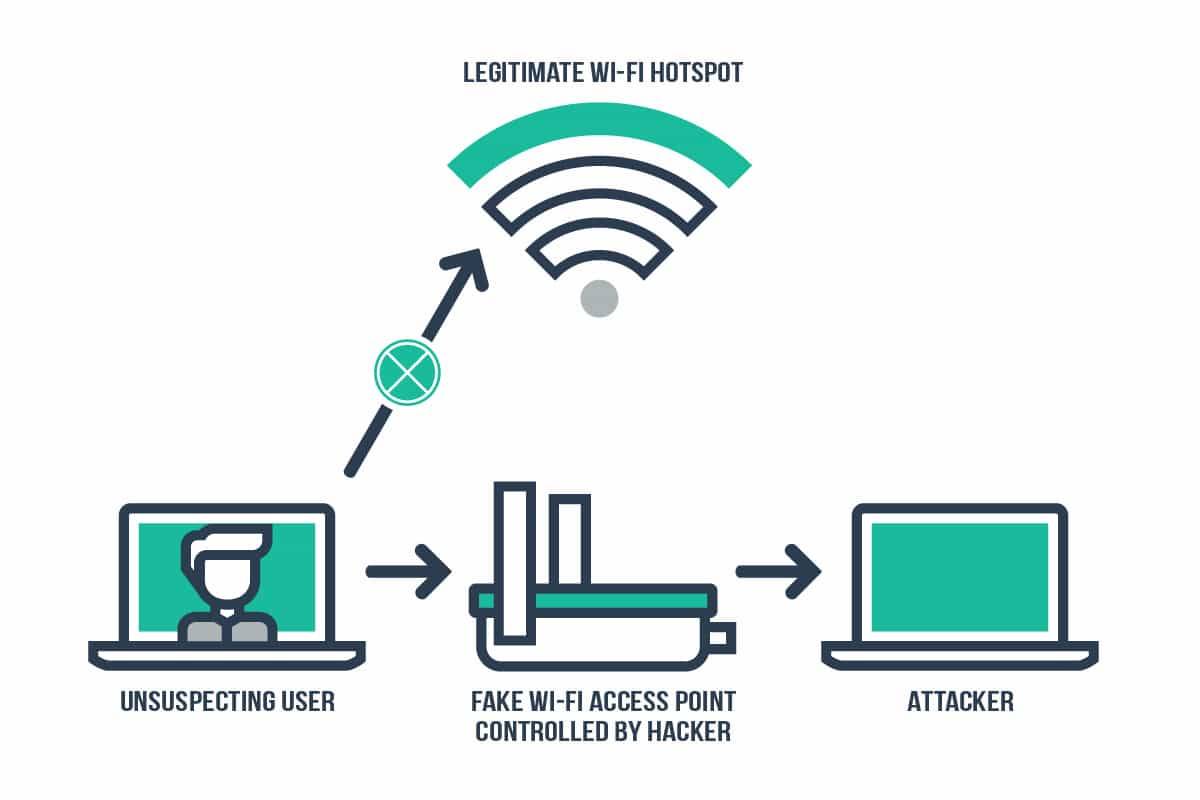


![PDF] Evil Twin Attack Mitigation Techniques in 802.11 Networks | Semantic Scholar PDF] Evil Twin Attack Mitigation Techniques in 802.11 Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c7f8f05a26716f23022a0a028a628962a1a06612/2-Figure1-1.png)

